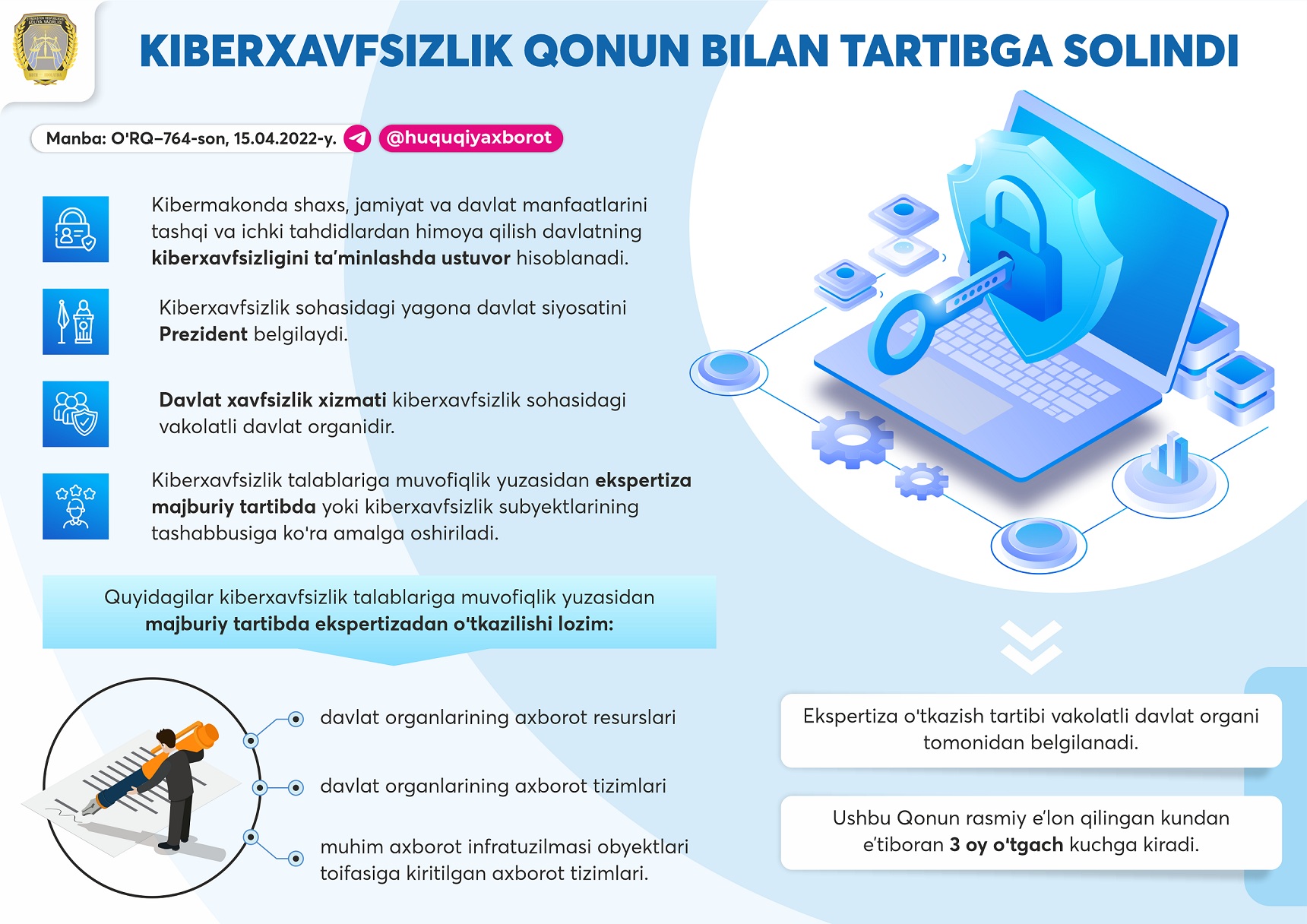

The Law "On Cyber Security" (No. 764, 04/15/2022) was signed by the President.
The law defines the main concepts in the field. According to him, cybercrime – is a set of crimes committed in cyberspace with the use of software and technical tools in order to acquire information, change it, destroy it or disable information systems and resources.
Cyberspace – is a virtual environment created with the help of information technologies. Also, many other necessary terms are explained in the law.
According to the law, protecting the interests of individuals, society and the state from external and internal threats in cyberspace is a priority in ensuring the state's cyber security.
The unified state policy in the field of cyber security is defined by the President.
The State Security Service is an authorized state body in the field of cyber security.
According to the law, state bodies and organizations have the right to receive information about cyber threats, vulnerabilities in software, equipment and technologies from the authorized state body in order to ensure cyber security.
Ensuring the preservation of information systems and resources of state bodies and organizations is carried out by creating backup copies of the information, the storage period of which should not be less than the last 3 months.
Expertise on compliance with cyber security requirements is carried out in a mandatory manner or at the initiative of cyber security subjects.
The following must be subject to mandatory examination for compliance with cyber security requirements:
• information resources of state bodies;
• information systems of state bodies;
• information systems included in the category of important information infrastructure objects.
The procedure for the examination is determined by the authorized state body.
Information about vulnerabilities, cyberthreats, cyberattacks and other malicious actions, as well as information objects found in information systems and resources, may be disclosed with the permission of the cyber security entity after appropriate measures have been taken to protect them.
This Law shall enter into force 3 months after its official publication.